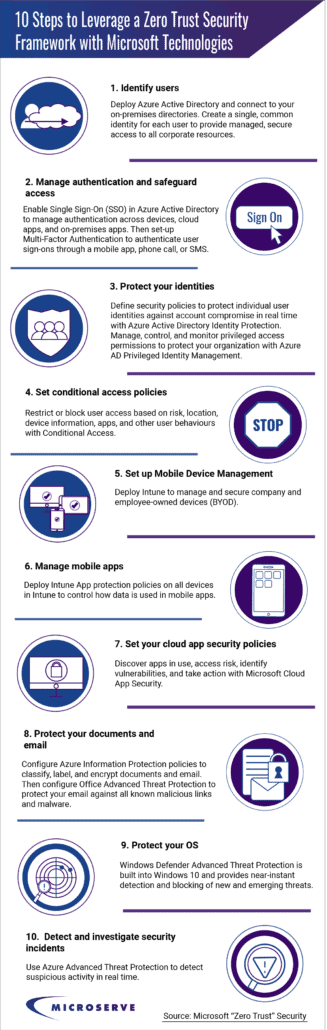
Since January, there has been an increase of 30,000% in phishing, malicious websites, and malware targeting remote users—all related to COVID-19 (Source). As the number of attacks increases and evolves, today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, apps, and data wherever they’re located. Many organizations were able to securely deploy their remote workforce by transitioning their existing network infrastructure and capabilities to a Zero Trust security framework.
The Zero Trust framework empowers organizations to limit access to specific apps and resources only to the authorized users who are allowed to access them. Read on to understand the 10 steps that you could leverage to secure your network using Microsoft 365 and Microsoft Azure AD.
Ready to learn more? Contact us today for a consultation or call 1-800-661-7783 to speak to one of our Accounts Managers.
Infographic